Microsoft 365 reminder
Microsoft announced in April 2020 the release of its latest bundle, Microsoft 365, which brings together Office 365 (Microsoft's collaboration suite), Windows, and the mobility and security suite (EMS). Currently, Microsoft 365 E5 offers over 26 security and compliance solutions.
Microsoft 365 security and compliance solutions are divided into six categories:
Security:
- Endpoint management
- Identity and access management
- Threat Protection
Compliance
- Data governance and protection
- Security posture
- SaaS application security management
How to effectively negotiate with Microsoft when transitioning to Microsoft 365 E5?
When considering the transition to Microsoft 365 E5, it is crucial to strategise your negotiation approach with Microsoft. In order to optimise your investment and ensure comprehensive security measures, we recommend including an advanced detection and response solution for Microsoft 365 in your purchase discussions.
By prioritising the inclusion of this solution during negotiations, you can avoid potential difficulties in investing in additional security measures after the completion of your Microsoft 365 E5 subscription. Integrating the advanced detection and response solution alongside your Microsoft 365 E5 licences will provide a more robust security infrastructure from the outset.
During negotiation periods, especially when upgrading to a premium licensing plan like Microsoft 365 E5, Microsoft is more inclined to make commercial efforts and support customers during the transition. Capitalising on this opportunity, you can leverage potential discounts offered by Microsoft to allocate funds for the purchase of a complementary security solution. This, in turn, will significantly enhance the visibility of attacks on the Microsoft 365 control plan.
Alternatively, without integrating a dedicated solution, you would need to create detection rules on your SIEM/SOAR to mitigate these risks. However, this approach would require additional investments and the results may not be as substantial as anticipated at this stage. Therefore, it is advisable to seize the negotiation phase as an opportunity to secure comprehensive protection for your Microsoft 365 environment.
Office 365 vs Microsoft 365
Microsoft 365 provides a range of licensing plans designed to cater to the diverse needs of businesses and organisations, facilitating their digital transformation. These plans are tailored for different entities, including education or operator plans, and there are also licenses available for users who specifically require access to web-based office services through Office E1.
However, many companies require thick clients for the office suite and thus opt to transition to Office 365 E3. It is crucial to carefully consider whether subscribing to the M365 E3 bundle or sticking with Office 365 E3 and adding supplementary services as needed is the most suitable choice for your organisation's requirements.
Office 365 vs M365 E3
Microsoft 365 E3 encompasses Office 365 E3, EMS E3, and WIN E3, creating a comprehensive package. Notably, EMS E3 includes Azure AD Premium, which is highly recommended for efficient identity management within the Microsoft ecosystem. It facilitates dynamic user management and enables conditional access, simplifying endpoint provisioning. Customers who already utilise Windows Enterprise (Windows E3) view the M365 E3 bundle as an obvious choice, especially considering the significant discounts Microsoft offered during its launch to encourage migration.
The M365 E3 bundle provides an integrated suite of security and compliance features, empowering organisations with essential functions for securing and ensuring compliance across Office 365, Windows operating systems, and mobile fleet management through Intune.
Prominent services include Exchange Online Protection (EOP), offering safeguarding against phishing attempts and known malware. Additionally, the bundle offers classification and retention capabilities for unstructured documents within the office suite, complemented by Data Loss Prevention (DLP) measures. Furthermore, organisations undergoing eDiscovery investigations can leverage this service, which is accessible through M365 E3.
M365 E3 vs M365 E5
When comparing M365 E3 and E5 regarding security and compliance, the main distinction lies in the inclusion of native Microsoft security and compliance solutions. These solutions can also be obtained from third-party vendors like EDR, CASB, and Advanced Threat Protection for Office 365. Additionally, M365 E3 offers advanced service features like automated classification and advanced eDiscovery.
While most Office 365 E3 users will choose to subscribe to M365 E3, the number of organisations opting for M365 E5 will be more limited. This is because selecting M365 E5 implies a preference for relying exclusively on Microsoft, even for solutions provided by other leading market vendors. It is important to note that this decision extends beyond technical considerations and carries strategic implications, as it establishes a strong dependence on a single vendor for comprehensive defence measures.
Useful sources
In addition to the official Microsoft documentation, there are two useful sources of information for a detailed description of the services offered for each licence plan, as well as the public prices for each.
Attacks on M365 and associated risks
Microsoft 365 environments are susceptible to various types of attacks, often involving a combination of on-premises and cloud elements.
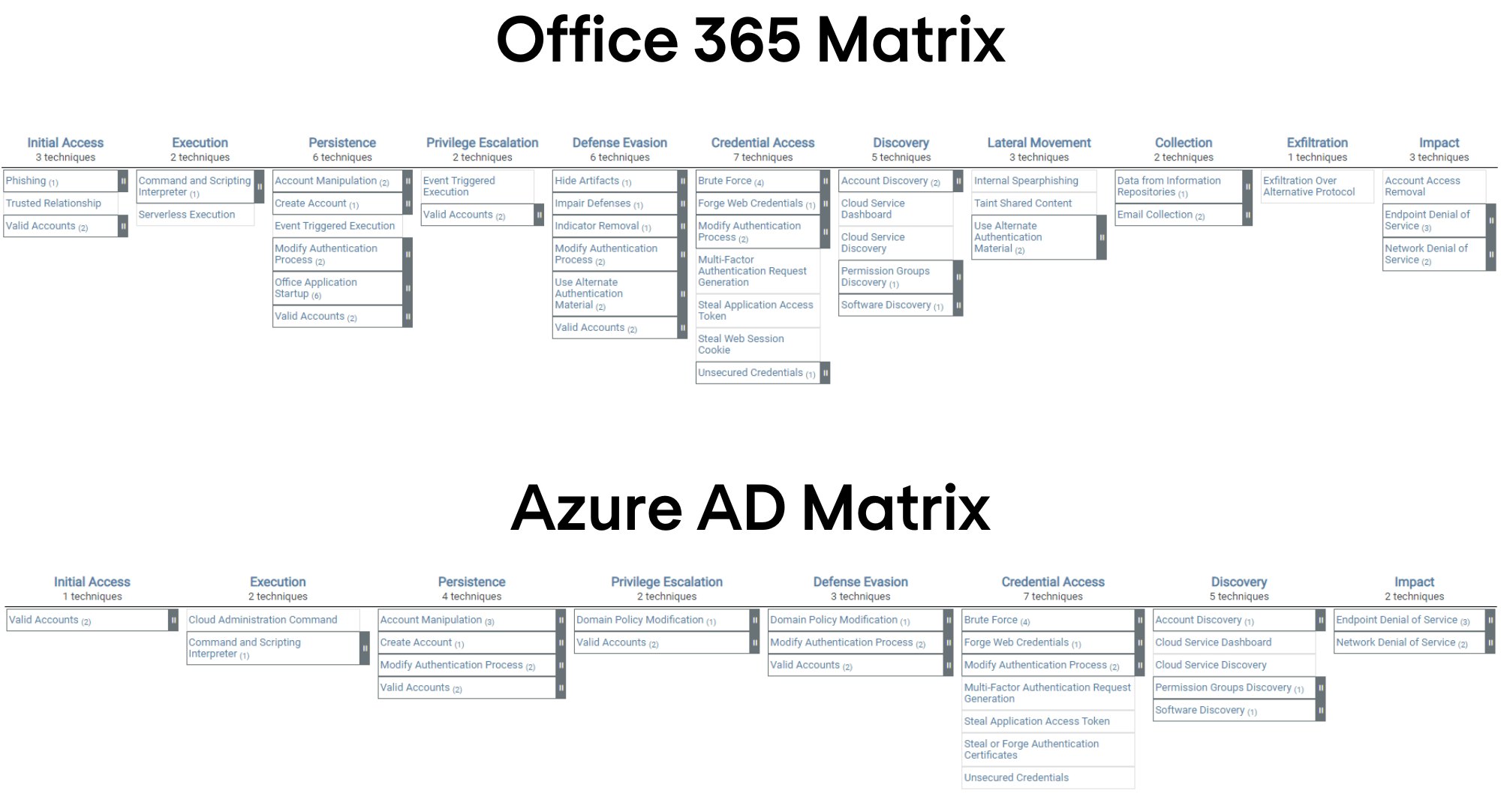
Attackers employ diverse techniques to achieve their objectives, and the MITRE ATT&CK® framework for Office 365 and Azure AD serves as a valuable resource for understanding these methods.
Common attacks on Microsoft 365 tenants include:
- Account brute force and MFA bombing to gain unauthorised access to an account.
- Utilising Power Automate feeds for automating malicious activities.
- Modifying settings in Exchange Online, such as email forwarding and transport rules.
- Adding unauthorised guests to the tenant to gather sensitive information.
- Exploiting OAuth consents in O365 to access tenant data.
- Data exfiltration leveraging eDiscovery functionality.
Rather than generating alerts for every individual malicious activity, it is crucial to focus on correlating these activities with each other. This correlation enables the detection of a chain of malicious actions, indicating an ongoing attack and warranting further investigation and analysis. Managing a high volume of individual alerts would be challenging, making the correlation approach more effective in identifying potential threats.
MITRE ATT&CK® Matrix for Enterprise
Below are the tactics and techniques representing the MITRE ATT&CK® Matrix for Enterprise covering cloud-based techniques for Office 365 and Azure AD. View the images in a larger size:
How can security be strengthened on Microsoft 365?
Detecting and analysing attacks requires linking suspicious activities together, rather than generating individual alerts for each activity. This approach prevents an overwhelming number of alerts that would be challenging to manage effectively.
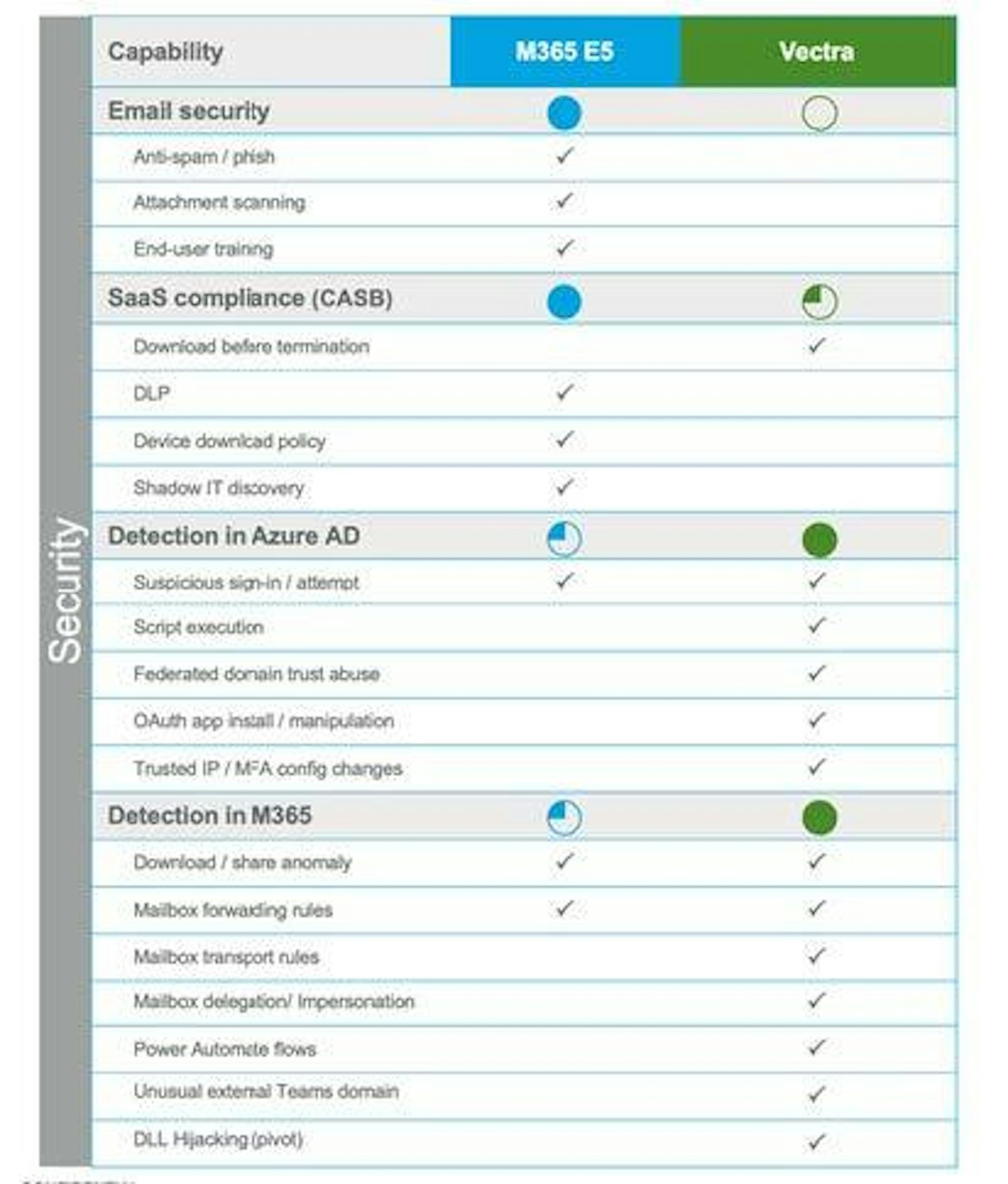
To enhance the detection of activities that could result in data exfiltration, it is recommended to leverage the attack techniques outlined by Mitre and the security coverage provided by Microsoft 365 E5. Specifically, monitoring Microsoft-related activities that could lead to exfiltration is crucial.
While information classification is an effective strategy to mitigate exfiltration risks, it's important to recognise that certain protection features, such as eDiscovery functions, can potentially be circumvented by attackers. Thus, it is necessary to strengthen detection capabilities beyond the rules offered by Defender for Cloud Apps, which may be limited and generate excessive noise.
There are four primary reasons for augmenting Microsoft 365 and a SIEM with additional security features:
- M365's security features have limited coverage of privileged user management activities.
- M365 audit logs and activity logs contain a vast amount of information.
- Default detection rules in SIEMs produce numerous false positives.
- Creating relevant detection rules incurs high costs, potentially reaching several thousand euros per rule.
However, investing in supplementary security solutions to fortify Microsoft 365 can be complex, particularly for organisations that have recently subscribed to Microsoft 365 E5. This substantial investment entails a deployment timeline spanning multiple years before the expected benefits can be fully realised.
Vectra Detect solutions for M365 and Azure AD
Vectra is a specialised company that focuses on providing advanced detection and response solutions for network security. Vectra's offering, known as Vectra Detect for Microsoft 365 and Azure AD, delivers automated threat detection and response capabilities specifically designed for these cloud-based environments.
With Vectra Detect for Microsoft 365 and Azure AD, businesses can effectively identify and respond to sophisticated threats that target cloud services. For example, it can detect activities such as unauthorised access using stolen credentials to gain entry to sensitive information. Leveraging machine learning and artificial intelligence, the platform learns normal user behaviour and detects suspicious actions that deviate from established patterns. Additionally, it can automatically take action to mitigate threats, such as blocking access to certain services or resetting user accounts.
In summary, Vectra Detect for Microsoft 365 and Azure AD provides a powerful solution for detecting and responding to threats in cloud-based environments. This capability is crucial for ensuring the security of business information and data.
Vectra.AI benefits for M365 and Azure AD threat detection
1. Advanced threat detection
Vectra.AI utilises advanced machine learning and artificial intelligence to identify suspicious activities that may indicate a threat. This includes detecting unusual login attempts, misuse of access privileges, and activities that do not align with a user's typical behaviour.
2. Speed of detection
Vectra.AI's platform is designed to quickly detect and respond to threats, enabling businesses to promptly react before further spread and damage occur.
3. Automatic response
In addition to detecting threats, Vectra.AI can automatically respond to them. For example, it can log out a user automatically or block access to specific services to limit the potential damage.
4. Flexibility
The platform is flexible and can be tailored to an organisation's specific security needs. It can be configured to detect specific threats or take specific actions in response to a threat.
5. User-friendly
The platform is designed with user-friendliness in mind, featuring a clear user interface that is easy to navigate. This allows users to quickly gain insights into the security of their cloud environments and take prompt action when necessary.
Overall, Vectra.AI provides a powerful solution for detecting and responding to threats in M365 and Azure AD, which is crucial for safeguarding business data and information.
Our team is ready for you
Do you want to know more about this topic? Leave a message or your number and we'll call you back. We are looking forward to helping you further.