Is outsourcing to a Nomios SOC right for you?
Organisations face several challenges related to cybersecurity that may lead them to consider implementing or outsourcing a Security Operations Centre (SOC). This page is intended to give an overview of our UK SOC, approach, capability and processes.
If any of the challenges below resonate with you, then a SOC could be the right approach; if so, get in touch and we will be happy to share our knowledge and experience, and provide straightforward advice.
Increasing complexity of threats
Compliance requirements
Lack of in-house expertise
Scalability issues
Resource constraints
Inefficient incident response
Integration of security tools
Visibility and monitoring gaps
Reputation management
Budget or cost control
Alert fatigue
Knowing best practice
Typical drivers for initial SOC consideration
Mandated compliance and maturing cyber threats continually put pressure on organisations and security professionals; typically, the growth combination of both, or the extreme of one, is an initial driver to outsource SOC services.
For example:
Increasing Complexity of Threats
- Challenge: Cyber threats are becoming more sophisticated and harder to detect.
- SOC Solution: Continuous monitoring and advanced threat detection capabilities offered by a SOC can identify and respond to complex threats.
Compliance Requirements
- Challenge: Stringent regulatory requirements related to data protection and privacy.
- SOC Solution: A SOC helps ensure compliance with laws and regulations like GDPR, HIPAA, and others by maintaining detailed logs and following industry standards.
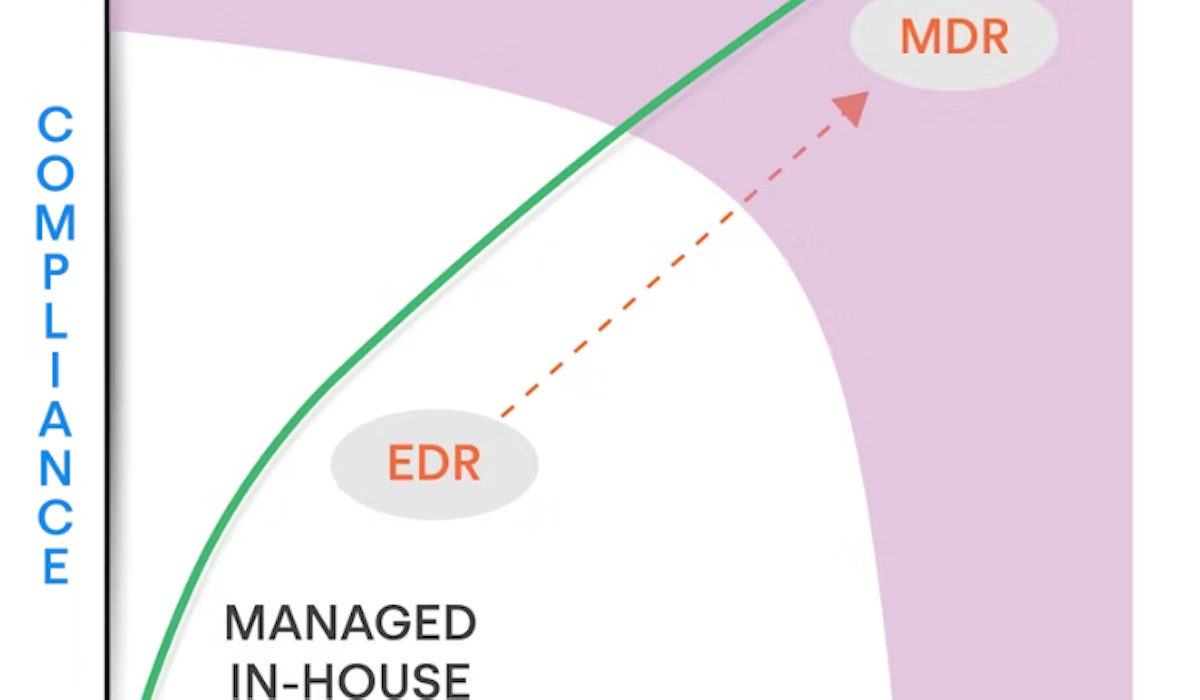
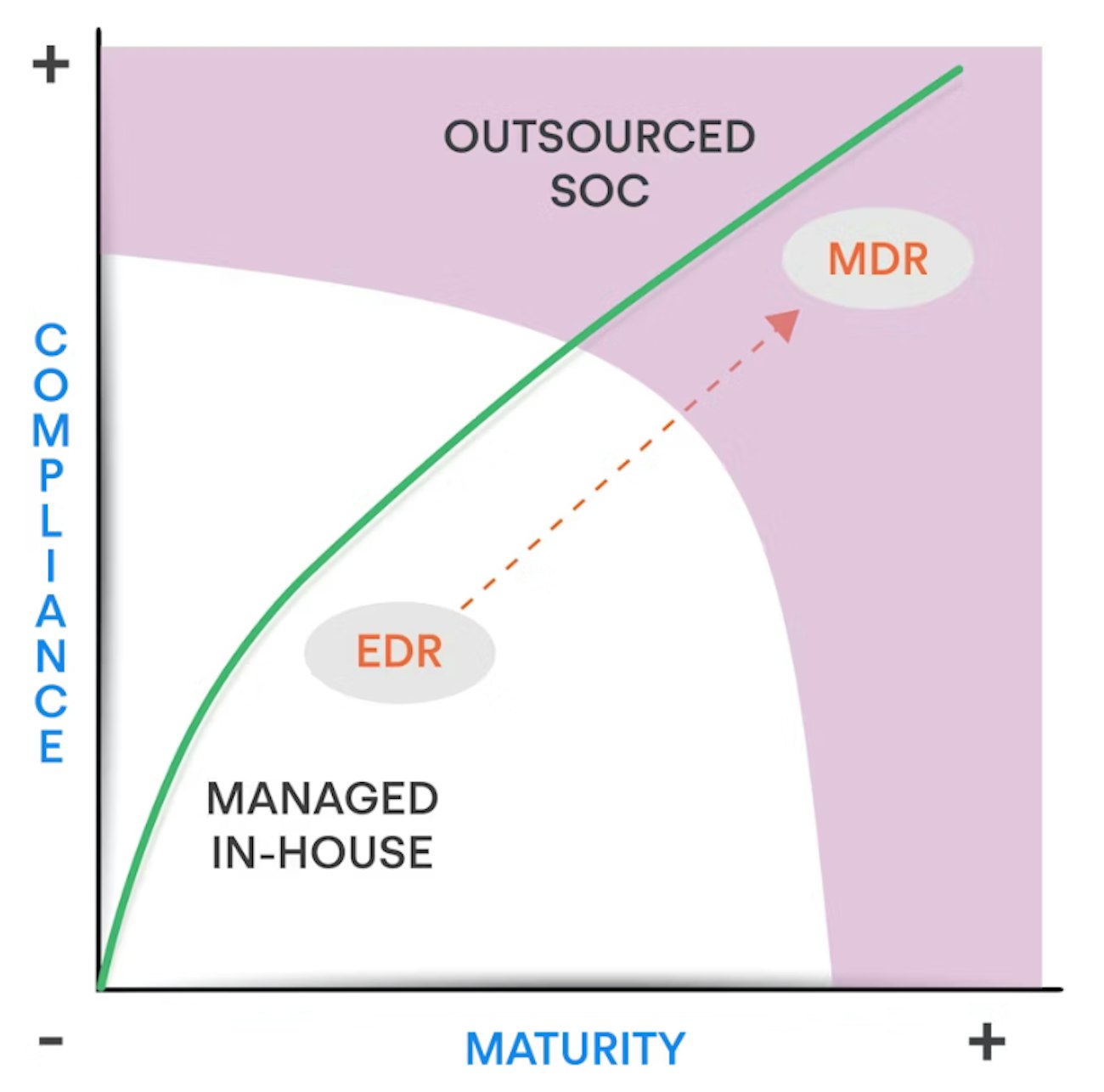
EDR is a good example of a cybersecurity control that is deployed by an organisation. It has often proved more difficult to integrate, manage or monitor than initially thought.
Outsourcing your own EDR solution* as an MDR to the Nomios SOC means you could benefit from an existing investment. And have peace of mind that your organisation is being protected.
* Please contact Nomios UK&I for EDR solution eligability
Our Managed SOC services process and structure
Log sources are essential for identifying anomalous and malicious behaviour within a SOC. They can originate from various systems, networks, security controls, cloud environments, and user activities, enabling comprehensive monitoring of potential threats to your assets. The collected log data is then utilised by the security operations tooling layer to enhance detection and response capabilities.
The tooling layer serves as a crucial aggregation point for various data types, including logging data, endpoint information, scanning results, and telemetry. This data is channelled into systems such as SIEM, EDR, or vulnerability management platforms, which are responsible for detecting malicious activities and generating alerts for the SOC's further analysis and response. From Nomios' perspective, we offer these services as a managed solution or can integrate event data from customer-managed platforms.
Once an alert is generated, it is sent to the SOC tooling layer, specifically the SOAR platform. SOAR coordinates, executes and automates tasks among various personnel and tools within a single platform. It ingests alert data and triggers playbooks to automate response workflows, reducing the need for level 1 analysts and allowing higher-skilled level 2 and level 3 analysts to handle alerts. Additionally, alerts are enriched with threat intelligence from sources like Mandiant, enhancing their context with indicators such as IP addresses, file hashes, or domain names.
The SOC performs various daily functions to support customers, including ongoing use-case development and tuning, which begins during service onboarding. When alerts are generated, they are investigated thoroughly; false positives lead to use case refinement, while legitimate incidents prompt further investigation and customer support for remediation if needed. The SOC also conducts proactive threat hunting to detect and mitigate potential threats that may have bypassed existing security measures. Regular meetings and reporting through the Service Delivery Manage ensure consistent communication and oversight of these activities.
Our service relies on the expertise and professionalism of our team, functioning as an extension of your in-house SOC. You will engage with named individuals, including the Service Delivery Manager, who oversees project management, reporting, SLA monitoring, and service reviews. The cyber security consultant supports onboarding and use-case development, while our skilled analysts focus on incident management, remediation, and threat hunting, with automation handling initial triage. The SOC Manager coordinates responses to cyber-attacks and participates in strategy meetings.
Our unique managed SOC approach
Knowledge of the client's risks, its technical environment and its organisation is essential for the SOC to be able to carry out all its activities. We carry out an initial assessment of your environment to understand your organisation, your technical context, your business and the associated risks.
This insight enables us to prioritise risk coverage with you and control the "Time-To-Detect" of the serious threats to your organisation.
"A balanced approach between the newest technology and the addition of "scenarios" allows us to optimise the incident timeline by improving both detection and remediation capabilities. This is why, as part of our business and our duty to advise, we strive to remain very pragmatic about the budgetary efficiency (CAPEX/OPEX) inherent in covering your risks." - Avinash Shet, Senior SOC Analyst
Efficiency is maximised by the close proximity between the customer and Nomios. The customer has direct access to our analysts who will work hand in hand with the customer's operational security and production teams, for which Nomios is a true extension.

Protect your organisation, and your network
As the volume and complexity of cyber attacks accelerate, Security Operations Centres (SOCs) have become the focus for bringing together the people, processes and technologies needed to defend and respond to the attacks on an organisation.
However, most IT and business managers do not know the true level of risk, and many have no visibility into the full range of potential vulnerabilities that could be exploited, let alone the means to fix them.
But organisations can keep abreast of modern threats by using a managed SOC. An effective SOC improves an organisation's incident detection and response capability while accelerating and improving its security posture.

Work process is agile and iterative
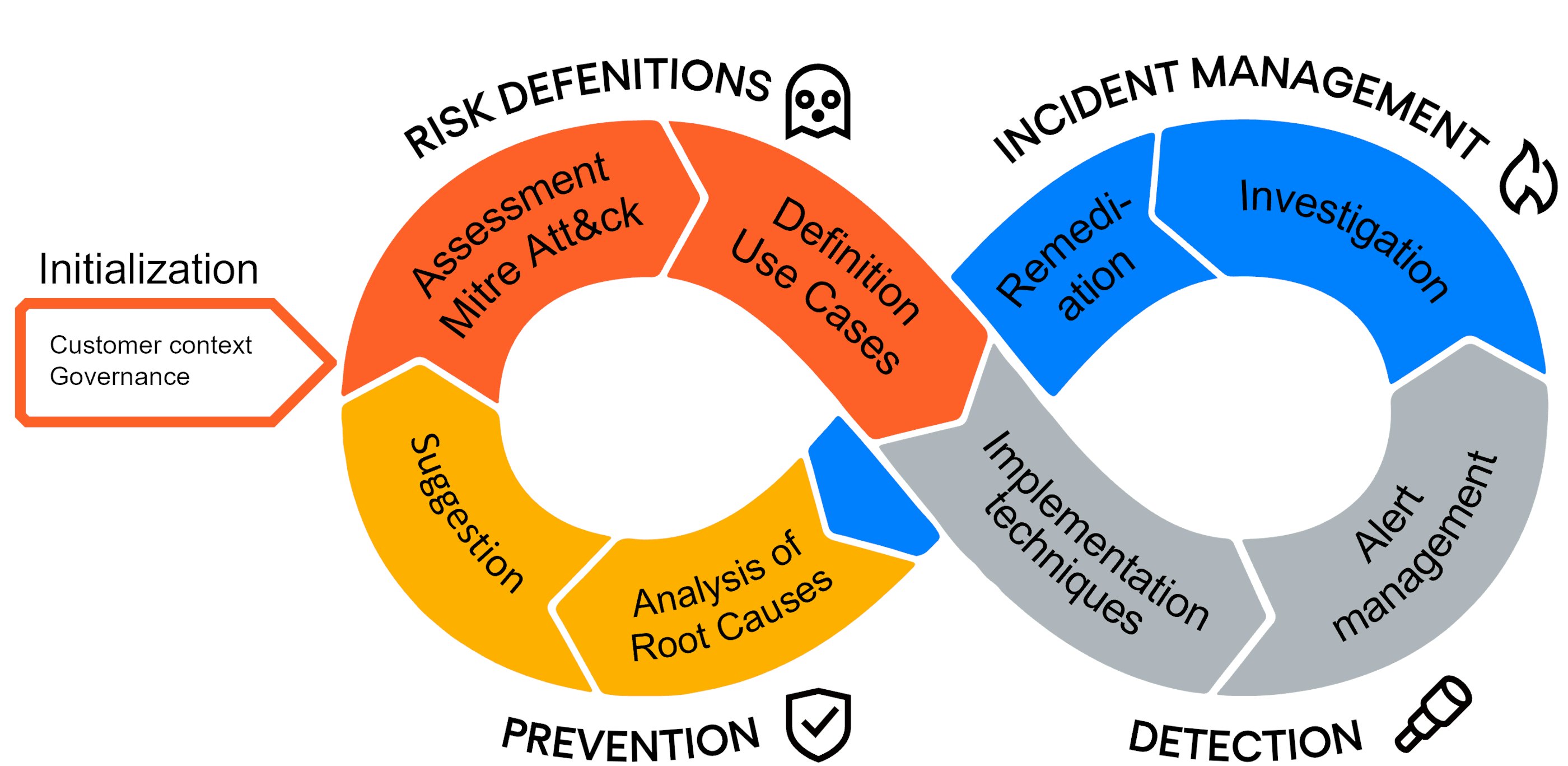
This agile model is the pillar of our operational security approach. It governs the quality of our offer through the iterative prioritisation of your risks, the pragmatic and total implementation of your use cases, and making the most of existing infrastructures in a continuous improvement process. The risk-based approach is the backbone of the service. We re-evaluate the risks at each iteration of the agile approach.
How we work with our customers
1. Initialisation phase
The initialisation of the service allows Nomios to get to know the technical, functional and organisational context. This discovery of your environment and your specificities is done through workshops covering your organisation and the personnel with whom the SOC will work.
This phase also allows us to frame the governance of the service with the final versions of the Service Agreement, Quality Assurance Plan and Security Assurance Plan.
2. Assessment phase
Cyber risk analysis based on the Mitre Att&ck model:
- External risk assessment, based on multiple cyber threat intelligence sources. Qualification of the real risks to the organisation.
- Internal defences: analysis of your internal security situation, including policy, security tools and organisational structure.
- Consolidation: the cross-referencing of all this data will make it possible to highlight the techniques most at risk for your organisation and thus define the priorities in the actions to be taken.
3. Detection phase
This step consists of the technical implementation of the use cases in the existing security components: SIEM/XDR, EDR, NDR and SOAR.
4. Incident management phase
After enriching the alerts (investigation, sandboxes), the correlation of indicators and the history of alerts known by the SOC makes it possible to refine the criticality of the alert to qualify it as an incident.
5. Prevention phase
Monthly analysis and consolidation of incidents in order to highlight recurring incidents. The re-evaluation of Mitre Att&ck risks and the search for root causes allow us to propose improvement plans at each iteration of the process.
A critical part of any managed SOC is the onboarding process – which we call The Shared Journey. The Journey shows the patch in which the client will take in order to get fully onboarded and live with the Nomios SOC.
The Journey consists of 6 workshops which can be delivered in person or remotely. Get in touch with our SOC team to find out more.
Read more about our network overlay support services
Reduce the complexity and cost of threat detection and incident response.
Having a dedicated managed SOC offers multiple benefits to your organisation. It's not just about detecting incidents, but also about analysing and proactively hunting down threats to help prevent attacks from happening in the first place. Discover the unique benefits of our managed SOC service.
Full security monitoring 24x7
- Security monitoring of advanced cyber threats on networks, on-premises, public cloud environments, SaaS applications and endpoints.
Responds to threats faster
- Nomios SOC analysts identify and validate threats, working with your incident response team to guide, automate response and remediation.
Keep an eye out for the latest threats
- Detects emerging and evolving threats with continuously updated threat intelligence.
Controlling the SOC budget
- All the benefits of a SOC while controlling the cost, complexity and time investment of an in-house operation.
Advanced analysis and machine learning
- A modern security platform combines advanced qualitative tools based on machine learning algorithms, data mining tools and simulations with traditional data query and consultation approaches.
Adopt an adaptive security architecture
- Static security architectures are outdated and inefficient. Our adaptive security architecture is able to prevent, detect, react and predict.
Frequently asked questions
Yes, establishing and maintaining a Security Operations Centre (SOC) can be expensive, and the costs can vary widely depending on several factors. Here's a breakdown of some of the aspects that contribute to the overall expense:
1. Personnel Costs
- Hiring skilled cybersecurity professionals can be costly, especially in competitive markets.
- Continuous training and certification of staff to keep them up-to-date with the latest threats and technologies also add to the expense.
2. Technology and Infrastructure Costs
- The necessary hardware and software for monitoring, detection, analysis, and response can be expensive to purchase and maintain.
- Integrating multiple tools and platforms may require additional investment.
3. Facility Costs
- If an organisation opts for an in-house SOC, the physical space and related infrastructure (e.g., secure communications, redundant power) add to the costs.
4. Compliance Costs
- Ensuring that the SOC adheres to various regulatory requirements, industry standards, and certifications can entail significant investment in both time and money.
5. Ongoing Operational Costs
- Continuous monitoring and maintenance of the SOC, including software updates, hardware refreshes, and regular audits, contribute to ongoing costs.
6. Scale and Scope of Services
- The size of the SOC and the range of services offered can significantly impact the total cost. A larger, more comprehensive SOC will generally be more expensive.
Outsourcing to a Managed SOC
- As an alternative to building and maintaining an in-house SOC, many organisations choose to outsource to a managed SOC provider.
- Outsourcing can be more cost-effective, as it allows access to specialised expertise, tools, and infrastructure without the need for significant capital investment.
- However, the costs for outsourced SOC services can still be substantial, depending on the level of service, SLAs, and other contract terms.
Conclusion
SOCs can be expensive, and the decision to implement one should be carefully considered in light of the organisation's specific needs, goals, and budget. While the costs are substantial, the value provided in terms of enhanced security posture, risk mitigation, compliance management, and potential prevention of costly breaches should also be weighed in the decision-making process.
Organisations should carefully assess their requirements and explore various options, including in-house and outsourced SOCs, to find a solution that aligns with their budget and security needs.
As organizations scale and compete, protecting endpoints, assets and data from exfiltration, breach or other risks becomes paramount. The complexity of the security landscape has changed dramatically over the last several years, and organizations need to stay ahead of a rapidly changing threat landscape.
Many organizations now seek to outsource parts or all of their security functions to a trusted security provider. Managed security services (MSS) is a service model or capability provided by security service providers to monitor and manage security solutions, networks, systems, and even software-as-a-service (SaaS) applications and cloud environments.
MSSPs provide an array of skilled professionals, such as onboarding specialists, security analysts or service delivery experts, engineering and support, project management and customer service. More specialized roles such as incident response, threat intelligence and threat hunting can be added, depending on the desired scope of the engagement.
Get the best support for your business today
Extend your network team with our support services and address issues before they impact your business.

Discover more network overlay support services from Nomios
Our strength lies in our flexibility and focus on developing tailor-made solutions for our customers. Discover in which areas we can support your IT team.

MDR Managed Detection & Response
Advance your security operations capabilities while reducing mean time to detect and contain threats.

Managed firewall
Full management of your organisation’s firewall infrastructure.

Managed SIEM
Enterprise-grade SIEM to protect and secure your critical data from ever-changing cyber threats.