In an ever-evolving cybersecurity landscape, ransomware continues to represent one of the most formidable threats to organisations. In 2025, we are observing the continuation of a trend that began in recent years: the increasing sophistication of infiltration and execution methods. This article presents the mechanisms used by cybercriminals, particularly obfuscated code techniques and fileless attacks, and proposes appropriate defence strategies, particularly for managed SOC.
The Evolution of Ransomware: Towards Increased Stealth
According to the Controld report published in early 2025, fileless attacks continue to increase and are involved in a significant portion of security incidents. This evolution is explained by the effectiveness of these techniques in bypassing traditional security solutions based on signatures. In2023, "Living-off-the-Land" binaries were already used in 79% of targeted attacks, a trend that has continued since.
Attackers have gradually abandoned conventional methods in favour of more discreet approaches that are difficult to detect. The objective remains the same – encrypting data and demanding a ransom – but the means of achieving this have become considerably more sophisticated, requiring advanced detection capabilities to counter them.
Obfuscation Techniques: Hiding to Strike Better
Code obfuscation is a fundamental technique in the ransomware developer's arsenal. It involves deliberately making computer code difficult to understand for an analyst or automated detection system while preserving its malicious functionality.
Common Obfuscation Mechanisms
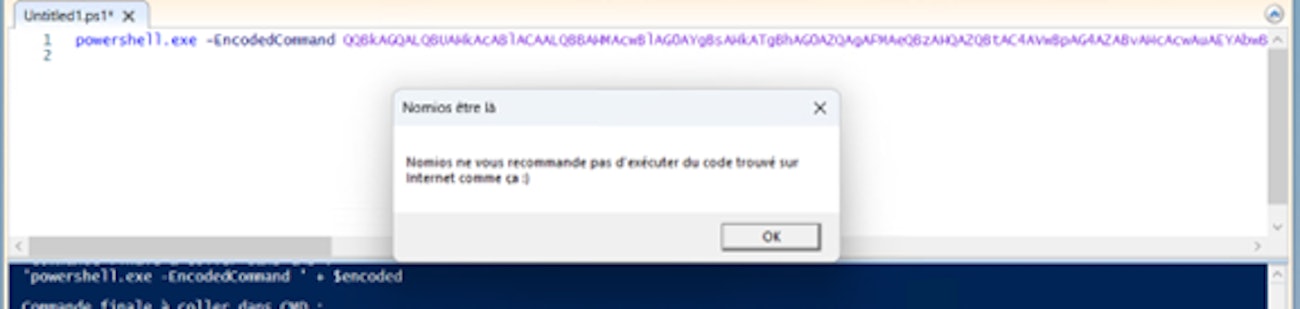
- Base64 Encoding: Transformation of code into seemingly random character stringsExample of Base64 obfuscated PowerShell command:
This code, once executed, displays a window with the message: "Nomios recommends not executing code you find on the Internet without analysing it".
powershell.exe -e powershell.exe -EncodedCommand QQBkAGQALQBUAHkAcABlACAALQBBAHMAcwBlAG0AYgBsA
HkATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVwBpAG4AZA
BvAHcAcwAuAEYAbwByAG0AcwANAAoAWwBTAHkAcwB0AG
UAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMALg
BNAGUAcwBzAGEAZwBlAEIAbwB4AF0AOgA6AFMAaABvAHc
AKAAiAE4AbwBtAGkAbwBzACAAbgBlACAAdgBvAHUAcwAgA
HIAZQBjAG8AbQBtAGEAbgBkAGUAIABwAGEAcwAgAGQAJwB
lAHgA6QBjAHUAdABlAHIAIABkAHUAIABjAG8AZABlACAAdABy
AG8AdQB2AOkAIABzAHUAcgAgAEkAbgB0AGUAcgBuAGUAdA
AgAGMAbwBtAG0AZQAgAOcAYQAgADoAKQAiACwAIAAiAE4
AbwBtAGkAbwBzACAA6gB0AHIAZQAgAGwA4AAiACkA
- XOR Operation: Application of binary operations between malicious code and a secret key. Among the most commonly used obfuscation techniques, the XOR (exclusive OR) operation stands out for its simplicity of implementation and effectiveness. This binary operation compares two bits and returns1 only if exactly one of the two bits is 1. To obfuscate code with XOR, attackers apply this operation between each byte of the malicious code and a secret key. The process can be repeated with different keys at various stages of the attack, creating a real puzzle for security analysts.
- Dead Code Insertion: Addition of useless instructions to complicate static analysis
- Polymorphism: Automatic modification of code at each execution while preserving its functionality
These obfuscation techniques allow ransomware to effectively bypass signature-based detection systems and considerably complicate post-incident forensic analysis work. As revealed by a recent ransomware analysis at Nomios, the de-obfuscation process can require significant time and resources, sometimes mobilising entire teams for several days. This is why outsourced SOC services are becoming essential for many organisations.
Anatomy of Fileless Attacks: The Invisible Threat
Fileless malware represents a notable evolution in the threat landscape. Unlike traditional ransomware that requires installing an executable file on the hard drive, these attacks operate entirely in memory, without leaving persistent traces on the file system.
Characteristics of Fileless Attacks
- Exploitation of legitimate tools already present on the system (Living off the Land)
- Direct execution in memory without writing to disk
- Frequent use of malicious PowerShell and the .NET framework
- Persistence via the Windows registry or scheduled tasks
These ransomware exploit legitimate tools already present on the system, such as PowerShell or Python, to execute their malicious payloads directly in memory. This "Living off the Land" approach (using native system tools) makes detection very difficult for traditional security solutions that focus on file analysis.
According to Halcyon.ai data published in early 2025, "Living-off-the-Land" techniques are now a defining feature of modern ransomware campaigns, allowing attackers to use legitimate tools for malicious actions while minimising their digital footprint. Detecting these attacks requires advanced behavioural monitoring solutions.
The Modern Attack Process: A Sequential Deployment
Modern ransomware attacks no longer occur in a single step but rather resemble a methodical sequence of actions, often spread over several days or even weeks to avoid detection. They resemble a criminal "advent calendar," where attackers deposit their payload in small pieces over several days to avoid detection.
Typical Stages of a Fileless Attack
- Initial Phase: Execution of a Base64 obfuscated PowerShell script, often via a malicious document
- Persistence Establishment: Creation of scheduled tasks or registry modifications
- Internal Reconnaissance: Gathering information about the network and identifying priority targets
- Lateral Movement: Propagation across the network by exploiting vulnerabilities or compromised credentials
- Memory Injection: Loading malicious code directly into legitimate process memory
- Data Exfiltration: Theft of sensitive information before encryption (double extortion technique)
- Final Deployment: Execution of the complete encryption payload
This sequential approach allows attackers to remain discreet until the opportune moment to deploy encryption, thus maximising the impact of the attack. To detect these complex sequences, specialised SOC teams use advanced event correlation techniques.
The Strategic Use of Malicious DLLs
Malicious DLLs play a central role in many modern ransomware attacks. These libraries, often developed in .NET, are themselves obfuscated to complicate analysis and can be loaded directly into memory without leaving traces on the disk.
The main functions of these DLLs include:
- Calling specific system functions
- Bypassing security mechanisms
- Facilitating lateral propagation within the network
- Executing encryption routines
As revealed by a recent incident blocked by the Nomios SOC, complete reconstruction of a malicious DLL can require several days of intensive forensic analysis work, even for seasoned experts.
Polymorphic Ransomware
Beyond obfuscation and fileless techniques, polymorphic ransomware represents a further advancement in sophistication. This malicious software has the ability to constantly modify its code and signature, making detection by traditional solutions almost impossible.
Polymorphic code is a program capable of automatically transforming itself while preserving its original functionality. In the context of ransomware, this technique allows the malware to generate unique variants of itself with each infection, thus evading signature-based detection systems.
Polymorphic techniques include:
- Code mutation during execution
- Use of random code generators
- Insertion of useless but harmless instruction sequences
- Dynamic reorganisation of functions
Faced with these evolving threats, modern security operations centres play a crucial role in protecting critical infrastructure.
Defence Strategies Against Advanced Ransomware
Faced with these sophisticated threats, organisations must adopt a defence-in-depth approach combining advanced technologies and human expertise.
1. Enhancing Behavioural Detection
- Deploy EDR (Endpoint Detection and Response) solutions capable of analysing behaviour rather than relying solely on signatures
- Enable advanced logging of PowerShell and scripts
- Implement behavioural anomaly detection systems
2. Limiting the Attack Surface
- Restrict execution of unsigned PowerShell scripts
- Apply the principle of least privilege to limit lateral propagation
- Segment the network to contain potential infections
3. Strengthening Digital Forensics Capabilities
- Develop skills in volatile memory analysis
- Implement network traffic capture and analysis tools
- Establish incident response procedures specific to fileless attacks
4. Integrating a Modern SOC
A Security Operations Center (SOC) equipped to detect and respond to advanced threats constitutes an essential element of defence against modern ransomware. Key capabilities of an effective SOC include:
- Continuous24/7 infrastructure monitoring
- Advanced behavioural analysis capabilities
- Expertise in detecting obfuscation techniques and fileless attacks
- Rapid incident response procedures
Expert Insights
Ransomware using obfuscated code and fileless attack techniques represent a major threat to organisations in 2025. Their increasing sophistication, combined with the adoption of polymorphic techniques, makes their detection and analysis increasingly complex.
For analysts and cybersecurity managers, understanding these advanced mechanisms is essential to implement effective defence strategies. Beyond technical solutions, it is a race for expertise between defenders and attackers that continues.
Faced with this constantly evolving threat, the most effective approach remains the combination of advanced SOC technology, high-level human expertise, and a security culture shared by the entire organisation.
Get in touch with our security experts
Our team is available for a quick call or video meeting. Let's connect and discuss your security challenges, dive into vendor comparison reports, or talk about your upcoming IT-projects. We are here to help.