Current challenges with threat intelligence
Security teams require deep context to quickly prioritise and respond to sophisticated attacks. Threat intelligence gives analysts an edge, but today’s approaches provide limited value to security operations because the methods are so complex. Teams must manually collect and incorporate multiple low-value feeds into the tools they use for investigation and response. They also must choose between feeds with limited visibility on narrow vertical or general-purpose commodity indicators with limited context. It’s time for a different approach.
The AutoFocus difference
AutoFocus gives you instant access to Palo Alto Networks massive repository of high-fidelity threat intelligence so you can consume it as a feed. Crowdsourced from the industry’s largest footprint of network, endpoint, and cloud intelligence sources, you get a unique insight into real-world attacks. Every threat is enriched with the deepest context from world-renowned Unit 42 threat researchers. Your analysts save significant time with intel embedded in any tool through a custom threat feed and agile APIs.
Features
High-fidelity intel sources
- Instant access to the massive repository of Palo Alto Networks threat intelligence crowdsourced from the largest footprint of network, endpoint and cloud intel sources.
Researcher-curated context
- Enrich every threat with the deepest context from world-renowned Unit 42 threat researchers.
Custom dashboards and reporting
- Get the insight you need with a highly customisable dashboard, reporting and alerting, all effortlessly tailored by you.
Powerful granular search
- Rapidly analyse threats by combining more than 130 search dimensions across billions of samples and trillions of artifacts.
Embedded intel everywhere
- Power up investigation and response efforts with high-fidelity threat intel, using pre-built integrations for Cortex XDR™, Demisto® and embedded intel cards for any third-party tool.
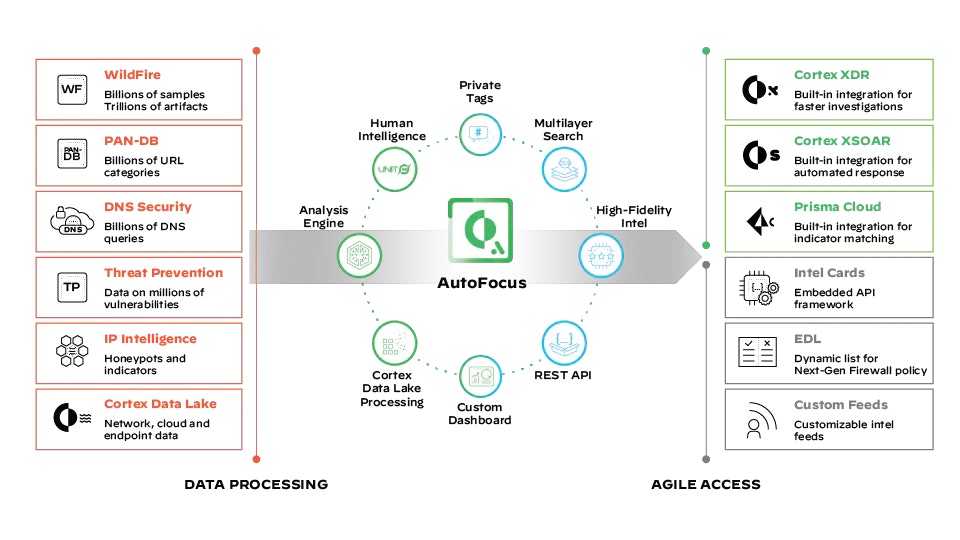
AutoFocus threat intelligence architecture
Access our continuously growing threat intelligence repository to get unique visibility into real-world attacks sourced from more than 65,000 enterprise customers over more than a decade.
Benefits
- Get unique visibility into attacks crowdsourced from the industry’s largest footprint of network, endpoint, and cloud intel sources.
- Enrich every threat with the deepest context from worldrenowned Unit 42 threat researchers.
- Give analysts a major time advantage with intel embedded in any tool through a custom threat feed and agile APIs
Unique visibility
Enriched context
Save time
Ready to talk?
Are you looking for pricing details, technical information, support or a custom quote? Our team of experts in Basingstoke is ready to assist you.