Global brands trust Mimecast to keep email protected
Deploy AI-powered email security trusted by 40K customers globally with Email Security, Cloud Integrated — an Integrated Cloud Email Security solution that blocks the most sophisticated email-based threats. Only Mimecast can combine the industry’s most powerful detection capabilities with instantaneous deployment, effortless administration, and optimised M365 protections from minute one.
Mimecast email security
Award winning benefits for all
- AI-powered, 40K customers, 1.3B emails inspected daily, 27K+ customers who use Mimecast alongside M365
- Deployment in minutes, optimised M365 protections out of the box
- Pre-configured settings, one-click remediation, intuitive threat dashboard
The Industry’s Best Detection
Instantaneous Deployment
Simplified Administration
Mimecast Email Security, Cloud Integrated
Mimecast’s new Email Security, Cloud Integrated is a gateway-less solution that is engineered for organisations that want to secure their M365 environment without adding complexity or burdening their already overstretched teams. Watch the video and find out more.
Mimecast’s Email Security, Cloud Integrated Interactive Product Tour
Explore how Email Security, Cloud Integrated makes securing your organisation easier than ever.
Mimecast Email Security, Cloud Integrated Demo
See Mimecast Email Security, Cloud Integrated in action.
Block email-based threats
Benefit from the next-generation of secure communications with:
- AI-powered detection
- Advanced phishing protection
- URL Computer Vision and deep scanning of destination URLs
- Advanced attachment scanning and detection
- Spam filtering
Optimise Microsoft 365 protection in minutes
Seamlessly integrate into Microsoft work environments:
- Fast, easy deployment
- Instantaneous learning
- Rapid identification of historic threats
- Purpose-built to enhance Microsoft Defender
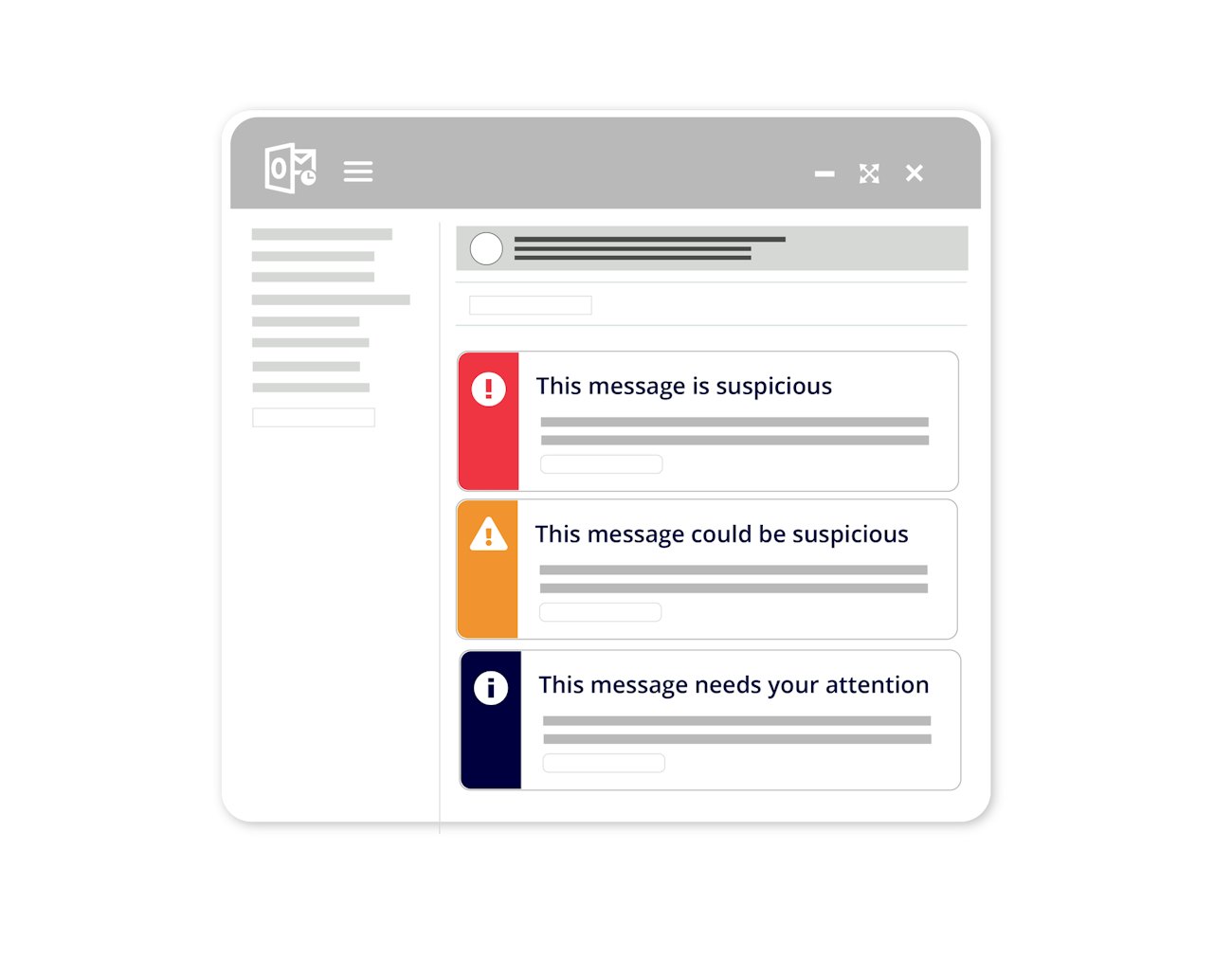
Empower end users with AI-driven email warning banners
Defend against highly targeted social engineering attacks with:
- Identity and social graphing for anomaly detection
- Contextual email banners surfaced based on risk and updated in real-time across devices
Simplify email security administration
Ease the burden on administrators and allow them to focus on mission-critical tasks with:
- Pre-configured settings
- Optimized protections out of the box
- Minimal configuration
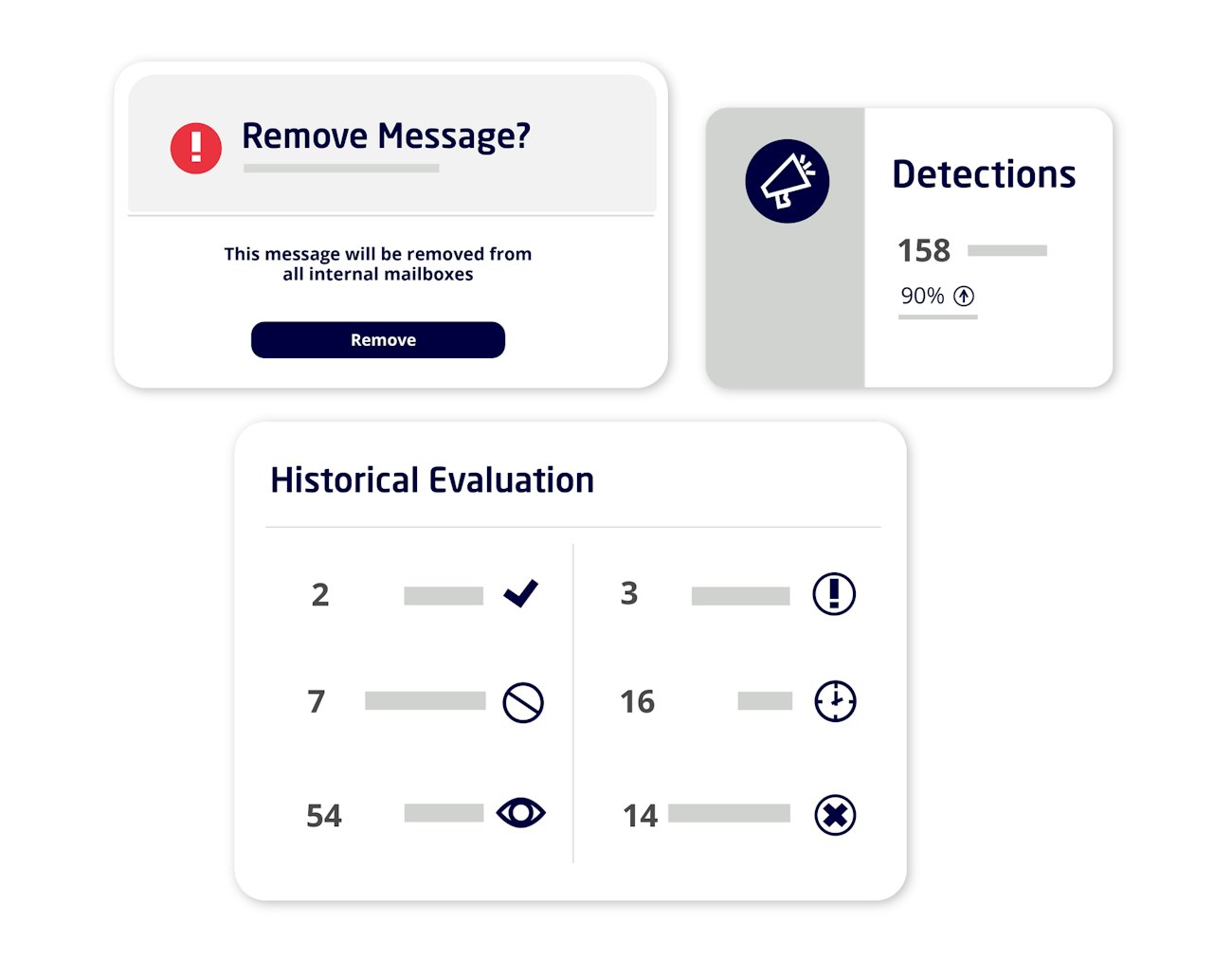
Get real-time intelligence on blocked attacks
Easily see, understand, and remediate:
- Threat dashboard that shows what’s been blocked and why
- Drill down capabilities for more detail
- Full visibility of email security risk posture
One-click remediation
Remediate with the click of a button.
- Fast, easy threat remediation
- Identification of historic email attacks
- Real-time visibility of blocked threats
Talk with our cybersecurity experts today
Our UK cybersecurity experts are available now for a call or video meeting. Let's talk about your network challenges, discuss solution suitability, or talk about vendor solutions or upcoming network projects. We are here to help.

Mimecast's latest resources for protecting business communication
Email security FAQs
Discover the 5 benefits of Mimecast email security.
Email is cybercriminals’ method of choice for entering business networks and stealing from them; email is also most organisations’ primary means of communications. Thus, email security safeguards employee communication and reduces risk with targeted threat protection, data leak prevention, and enforced email security controls. Multiple layers of email security protection are required to stop known and emerging email-borne threats before they reach your organisation’s environment.
Email is only as secure as organisations make it. Any IT department can spin up an email server, assign email addresses, and then let things run unchecked for users until there is a problem. Realistically, however, in today’s world of ever-increasing cyberattacks, securing email must be a top priority for every organisation. Most cyberattacks arrive via email. This means that not only does the IT department need to be on guard, but every single user in the organisation must be trained to look out for the threats that will arrive via their inbox. With the right set of integrated security tools and the right training, organisations can stop most email-based attacks before they ever launch. Email security takes time and takes effort, but it is not an impossibility with the right set of integrated tools and security awareness training.
Organisations are seeing a massive rise in cyberattacks. Legitimate business emails can contain the sensitive information cybercriminals need in order to access and exploit critical business systems. Phishing emails can give cybercriminals instant access to an organisation’s entire network in just one click. Even with proper email security training, data breaches can still occur. Organisations need cloud-based email solutions that offer encryption, targeted threat protection, data leak prevention, and enforced email security controls.
Organisations that need to strengthen their email security should start by taking the risks posed by cybercriminals very seriously. Organisations of all sizes across the world are being targeted daily by email-based attacks. These organisations need to start by building cyberthreat awareness across their entire organisation, not just in their IT department. Much of this can be accomplished through cyber awareness training programs. Organisations also need to do the research necessary to truly understand the specific threats they are facing, including conducting a complete audit of their current security tools. Once the organisation understands where they stand, they need to move forward with implementing security policies, enabling encryption at every endpoint, using threat intelligence to stay secure, and continually testing their ability to stop and recover from various types of cyberattacks. Organisations also need to govern user behaviour for tools, devices, and repositories, as well as tighten password policies and account access. Lastly, organisations need to look toward the latest advancements in technology, such as tools that use AI to recognise and share cyberattack information across their entire integrated security stack.
Organisations need an email security solution that stops malware, spam, and advanced threats using targeted threat protection, data leak prevention, and enforced email security controls. While team members should always be trained in proper email security, solutions need to be automated, cloud-based, and offer encryption. Email security solutions should work in the background and not impede user productivity. When evaluating email security companies, organizations need to find an email security partner with the right tools to prevent, detect, and respond quickly to phishing attacks and other email-based threats.
Your dedicated Mimecast experts
Nomios is an award-winning Mimecast partner with advanced specialities and the distinction of multiple certified engineers on staff. Our engineers are recognised by Mimecast as technical experts and advocates of Mimecast solutions. That means you can count on Nomios for the technical know-how and hands-on experience to accurately assess your business requirements, and design, implement, and manage a Mimecast-based solution to suit your needs.
Get in touch with our UK network experts
Our UK team is available for a quick call or video meeting. Let's engage and discuss your network challenges, dive into vendor comparison reports, or talk about your upcoming network projects. We are here to help.



















