Related insights
Top cybersecurity companies to watch in 2025
Read moreWiz CWPP: Comprehensive protection for hosts, VMs, containers & serverless functions
Securing cloud workloads with advanced protection
Wiz's Cloud Workload Protection Platform (CWPP) is expertly designed to address the complexities of cloud workloads, providing a spectrum of security measures from initial prevention to active, real-time detection and response.
The Wiz Way: A multi-Layered defense strategy
Wiz adopts a proactive approach in reducing the attack surface through its multi-layered defense strategy. The system provides agentless, full-stack visibility across entire cloud environments. Utilising advanced scanning technology, Wiz swiftly identifies vulnerabilities, exposed secrets, malware, and misconfigurations in VMs, containers, and serverless functions, significantly reducing workload risks.
A key feature of Wiz's approach is the real-time last line of defense. The Wiz Runtime Sensor enables internal monitoring of workloads, identifying threats or malicious activities as they occur. This allows for rapid and context-aware responses to emerging threats, substantially enhancing system security.
Moreover, Wiz integrates a unique policy that covers both Cloud and Code. This strategy shifts security focus earlier in the software development cycle, ensuring that workload issues are identified and addressed before reaching the production phase.
Wiz also offers unparalleled workload visibility. Its agentless discovery capability quickly identifies all cloud workloads without the need for deploying agents, compatible across various major cloud providers. The analysis extends beyond the surface level, encompassing all aspects of cloud workloads such as VMs, ephemeral resources, container registries, serverless functions, and virtual appliances. Wiz's comprehensive multi-layer analysis includes all configuration layers - cloud, operating system, host, and application - providing a thorough and holistic security assessment.
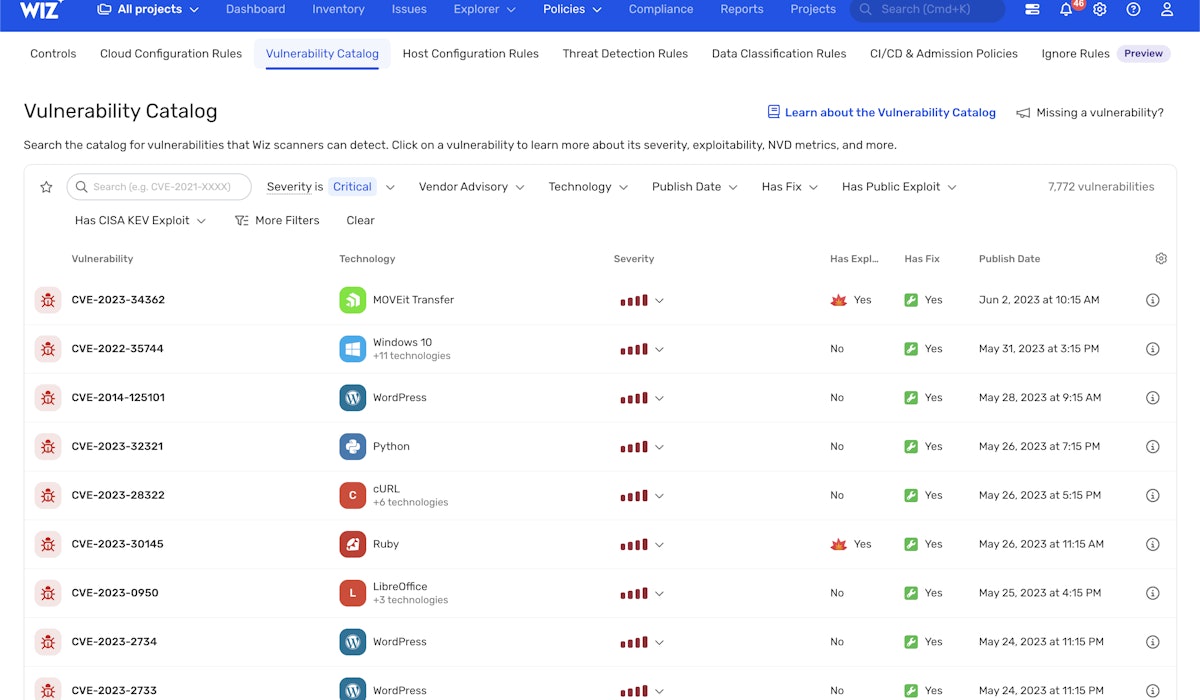
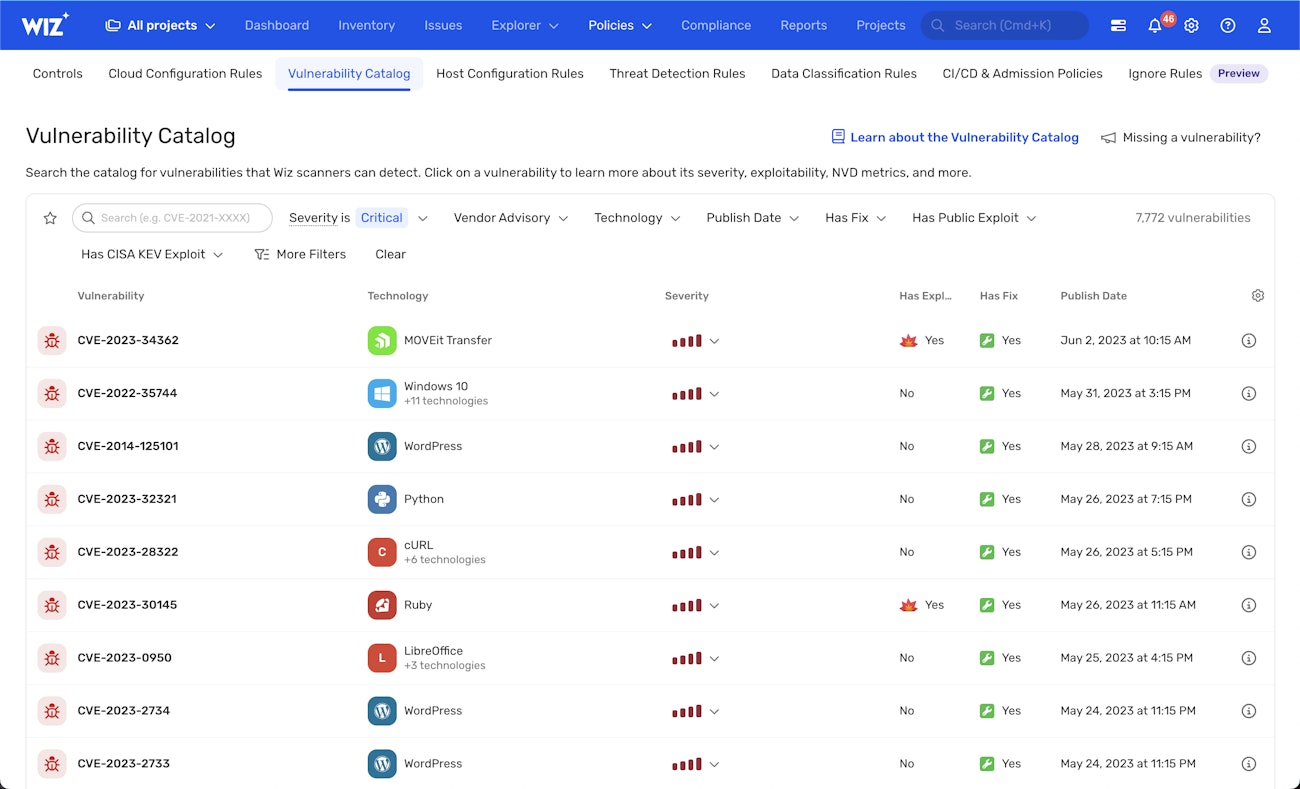
Efficient vulnerability prioritization with Wiz
Wiz's approach to managing security vulnerabilities is comprehensive and dynamic. Their extensive vulnerability catalog is constantly updated, capable of detecting over 70,000 vulnerabilities across more than 30 operating systems, including those listed in CISA’s KEV catalog. This vast database saves significant time and resources in identifying security threats.
A key aspect of Wiz's system is its contextual risk-based prioritization. This method addresses the common issue of alert fatigue by correlating vulnerabilities with a variety of contexts, such as public exposure, criticality, blast radius, and potential attack paths. This approach enables more efficient and targeted responses to security threats.
The Threat Center provided by Wiz offers immediate insights into workload vulnerabilities. This center is designed for quick identification of current security threats and streamlines the remediation process through one-click actions or automated rules.
Deep assessments for enhanced security
Wiz's platform includes comprehensive tools for enhanced security assessments:
- Secret Misuse Detection: Wiz's system is designed to protect against the compromise of crucial secrets by identifying unprotected secrets and related public data, including keys and certificates.
- Malware Prevention: Wiz actively scans VMs, container images, and serverless functions for various types of malicious software, bolstering defenses against malware threats.
- Sensitive Data Exposure Detection: The platform rapidly assesses both infrastructure and data for sensitive information like PII, PCI, PHI, or other secrets. This assessment is correlated with other risk factors to aid in the early detection and prevention of potential data leaks.
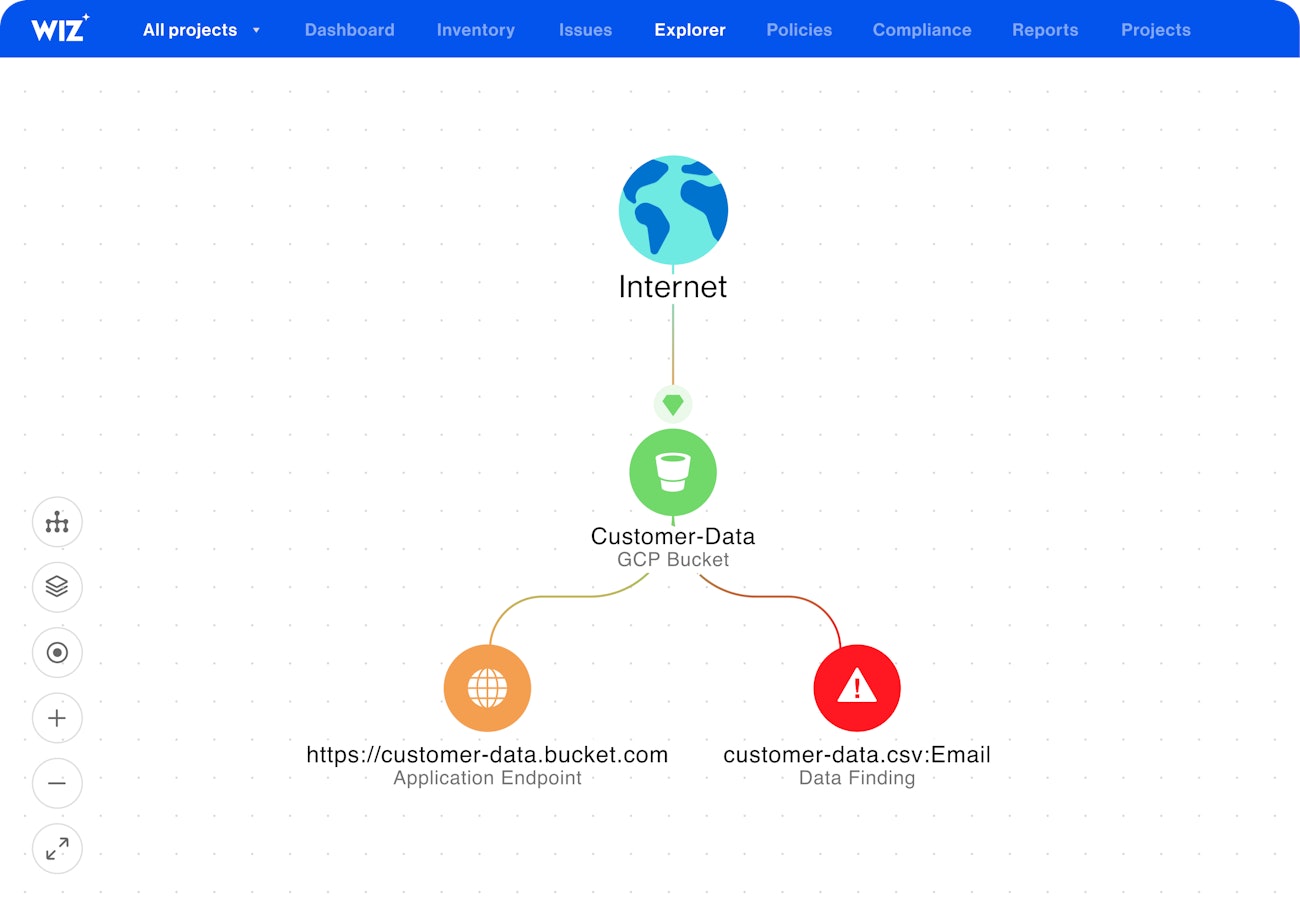
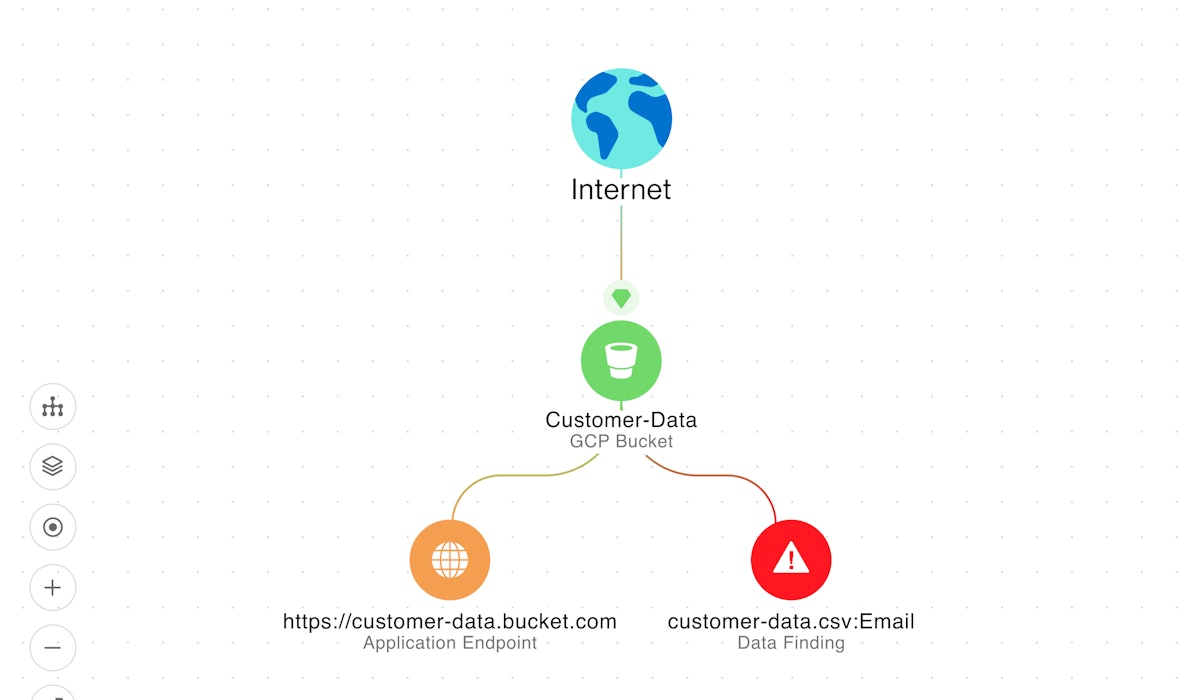
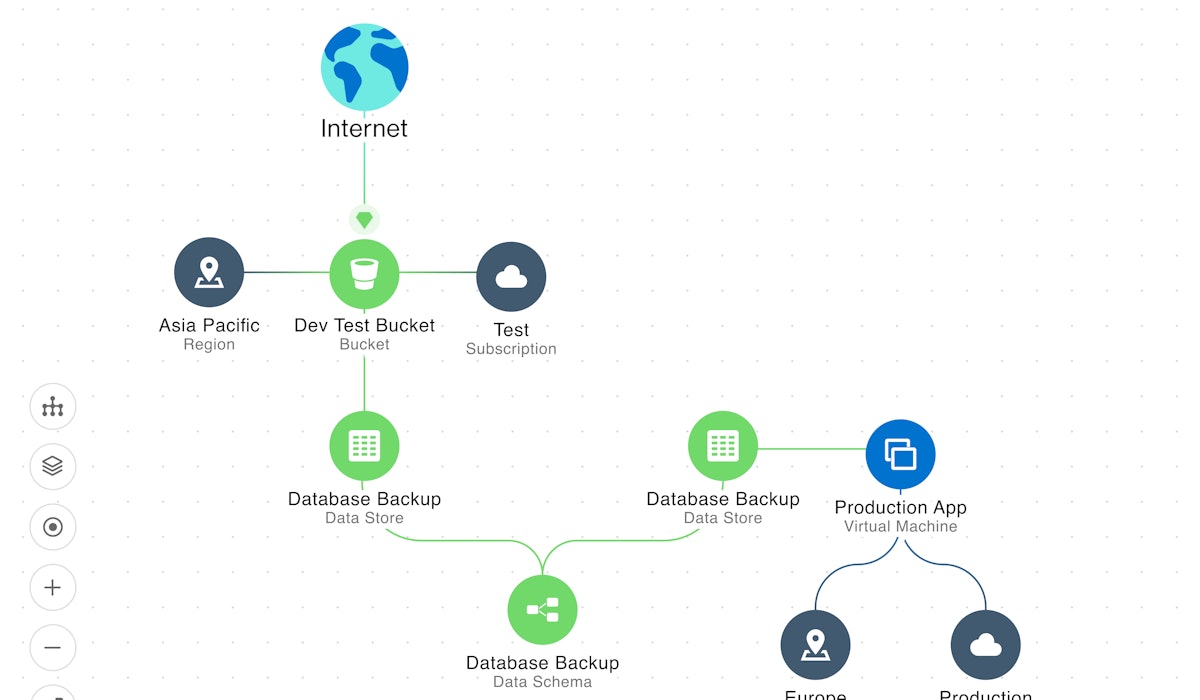
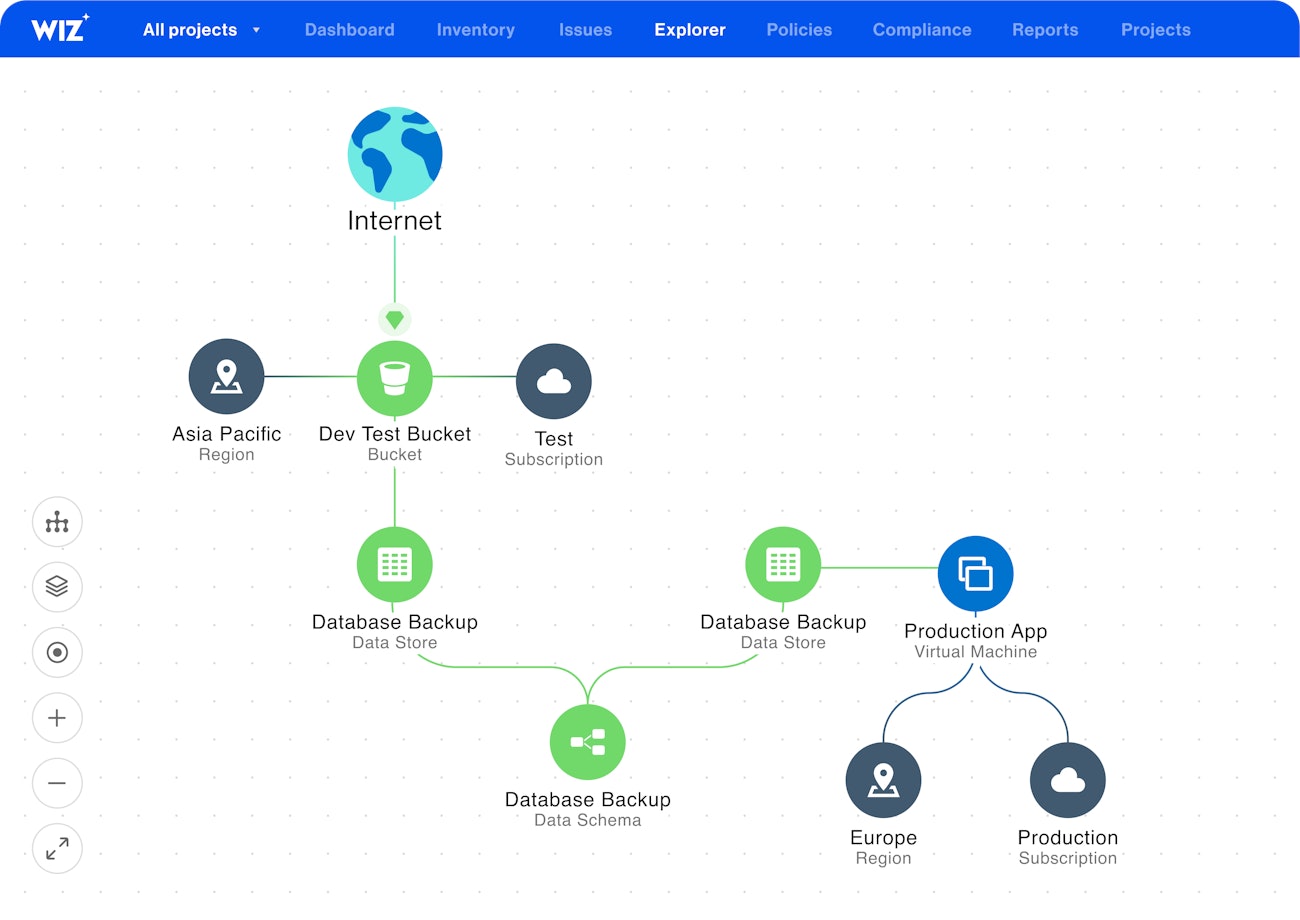
Advanced prioritization with context and visualization
Wiz's Security Graph is a standout feature, displaying the interconnectedness of technologies within a cloud environment and highlighting potential breach pathways. This tool allows users to visualize complex relationships and contexts from a single console, greatly aiding in security analysis.
Furthermore, the system enables the correlation of multiple risk factors, providing a comprehensive view of an organization's security posture. By analyzing both cloud and workload contexts, the tool assesses various aspects of the security landscape, including the attack surface and business impact risks. This thorough analysis helps organizations understand and address the vulnerabilities that pose the most significant threats.
Enhanced cloud workload security with Wiz's CWPP
Wiz's Cloud Workload Protection Platform (CWPP) serves as a reliable partner in securing cloud workloads. Known for its comprehensive, real-time, and context-aware approach, Wiz offers robust security solutions. Clients can trust in the protection of their hosts, VMs, containers, and serverless functions, ensuring that these crucial components are effectively safeguarded against a range of security threats.
Other solutions
Vulnerability management
Wiz provides an agentless, cloud-native vulnerability management solution with rapid threat detection and efficient pre-deployment scanning.
CSPM
Wiz provides comprehensive cloud security and compliance management across multiple platforms, with real-time misconfiguration detection and remediation.
Ready to talk?
Are you looking for pricing details, technical information, support or a custom quote? Our team of experts in Basingstoke is ready to assist you.