eXtended Detection and Response, in short XDR, sounds like you are protected anytime, anywhere. And it not only sounds that way, it actually is. Provided, of course, that you use a platform connected to your corporate network. When employees use private platforms that are not connected to the corporate network, the level of protection decreases significantly. This presents a critical challenge for you to address.
XDR offers extensive protection by collecting and automatically correlating data across multiple security layers—email, endpoint, server, cloud workloads, and networks. XDR allows for faster identification of threats, as well as investigation and response within a company's digital environment. It can be accessed at any time and from any location ("anywhere, anytime") for devices and networks that fall under its coverage.
Why do you need an XDR solution?
XDR is a key tool for companies, offering real-time monitoring and analysis of device activity to identify suspicious behaviour and quickly address threats. While not a legal requirement, using XDR can help companies meet regulatory standards (such as NIS2) by enhancing incident detection and response, thus minimising the impact of cyber attacks.
The importance of XDR is underscored by research from the Ponemon Institute, which found that almost 70% of breaches start from endpoints, highlighting the need for robust security measures. The rise of "bring your own device" (BYOD) policies increases flexibility but also introduces security risks without proper protection.
With 68% of organisations experiencing endpoint attacks that compromised data or IT infrastructure and an observed increase in attack frequency, it's clear that securing endpoints is critical. This scenario stresses the necessity of a strong security framework to protect corporate data accessed by a mix of office-based, remote, and hybrid workers on personal devices, illustrating the urgent need for comprehensive security solutions like XDR.
Factors to consider for your shortlist
When comparing XDR solutions to find the best fit for your organisation, focusing on the most critical aspects can help streamline your decision-making process. Here are the six important factors to consider:
- Integration and compatibility
- Detection and response capabilities
- Scalability
- Automation
- User experience and management
- Support and services
- Cost-effectiveness
To find the right XDR solution for your organisation, focus on these key factors. Consider how it can enhance your cybersecurity measures. Make sure it aligns well with your organisation's needs and resources.
One important factor for successful deployment and management of the XDR solution is having the right people on board. If you do not have security experts within your organisation, it is also an option to choose a managed XDR service or Security as a Service.
Best XDR solutions in the cybersecurity market
There are a large number of XDR solutions in the cybersecurity market available all with their own capabilities, integration features, reporting, and analytics. It is smart to select solutions depending on your specific enterprise needs, industry focus, and technological compatibility. Here are 6 XDR solutions that are popular in the business world, from partners we work closely with. For each XDR solution, we discuss six key aspects and two challenges they face.
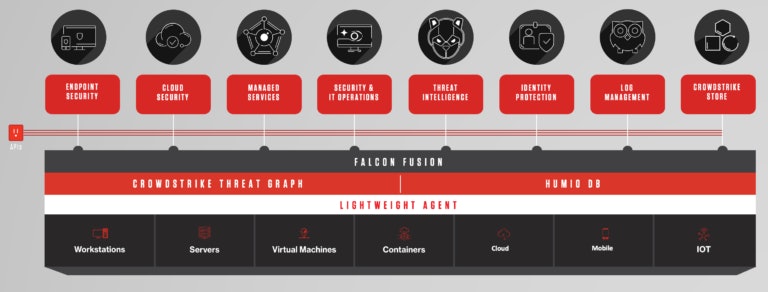
CrowdStrike Falcon
CrowdStrike Falcon is a highly regarded XDR solution, well-known for its comprehensive cloud-native security platform that delivers a range of cybersecurity capabilities designed to protect endpoints, cloud workloads, identity information, and more against advanced threats.
It is a part of CrowdStrike's broader suite of cybersecurity products, leveraging the power of the cloud to offer real-time protection and threat intelligence to organisations of all sizes. Here’s a closer look at some of its key features and benefits:
- Cloud-native platform: One of Falcon's most significant advantages is its cloud-native architecture, which allows for scalability, instant updates, and reduced hardware dependency. This approach ensures that organisations can adapt quickly to emerging threats without the burden of maintaining physical infrastructure.
- Single lightweight agent: The use of a single, lightweight agent simplifies deployment and minimises system impact. This agent provides multiple security functions, reducing complexity and enhancing endpoint performance, unlike traditional solutions that may require multiple agents or systems.
- Real-time threat intelligence: CrowdStrike Falcon leverages the CrowdStrike Threat Graph to analyse and correlate billions of events from across the globe in real-time. This global threat intelligence enables proactive threat detection and prevention, keeping organisations ahead of emerging cyber threats.
- Advanced threat detection and AI: With advanced analytics, artificial intelligence (AI), and machine learning, Falcon detects both known and unknown threats. Its predictive capabilities are designed to identify and mitigate zero-day exploits, ransomware, and sophisticated nation-state attacks effectively.
- Automated threat hunting and remediation: CrowdStrike Falcon automates the process of threat hunting and remediation, reducing the time from threat detection to resolution. This automation helps to lower the workload on security teams, allowing them to focus on strategic tasks and improving the overall security posture of the organisation.
- Comprehensive coverage: CrowdStrike Falcon extends its protection capabilities beyond just endpoints to cover the entire IT environment, including cloud workloads, mobile devices, and containers. This ensures consistent and comprehensive security coverage, regardless of where data resides or how it's accessed.
Two challenges that CrowdStrike Falcon faces:
- Integration complexity: Integrating Falcon XDR with existing security infrastructures and third-party tools may pose challenges, particularly in heterogeneous environments.
- Scalability: Ensuring scalability to support the increasing volume of data generated by large enterprises and high-traffic networks can be a challenge.
CrowdStrike Falcon is suited for enterprises looking for a robust, scalable, and efficient XDR solution that can protect against a wide range of threats with minimal overhead. Its emphasis on using advanced analytics and machine learning, combined with real-time threat intelligence, makes it a powerful ally in the fight against cybercrime.
Palo Alto Networks Cortex XDR
Palo Alto Networks Cortex XDR is a cybersecurity platform that enhances the ability of organisations to combat complex cyber threats. By extending traditional detection and response capabilities across endpoints, networks, and cloud services, it offers a holistic view of potential threats. Here are the six most impactful features of Cortex XDR:
- Cross-domain data integration: Cortex XDR excels in gathering and correlating data from multiple sources like network traffic, endpoints, and cloud data. This comprehensive visibility allows it to detect intricate attack patterns that might be missed when analysing data in isolation.
- Behavioural analytics: Utilising advanced behavioural analytics and machine learning, Cortex XDR detects malicious activities by examining the behaviours of users and network entities. This capability often identifies potential threats earlier than traditional, signature-based detection methods.
- Automated threat hunting and response: Cortex XDR enhances security efficiency with automated threat hunting, investigation, and response capabilities. It swiftly applies protective measures across the network, significantly reducing response times and the impact of incidents.
- Real-time security orchestration: Cortex XDR offers real-time security orchestration capabilities which allow organisations to quickly coordinate various security responses across different platforms. This feature ensures that security measures are triggered instantly and harmoniously across all protected systems, enhancing overall defence agility and efficiency.
- Proactive threat hunting: Beyond its automated capabilities, Cortex XDR provides tools for proactive threat hunting, enabling security teams to uncover and mitigate hidden threats before they evolve into major breaches.
- Simplified incident management: The platform streamlines incident management by consolidating alerts into a single interface. This helps security teams prioritise and efficiently respond to the most critical threats.
Two challenges that Palo Alto Cortex XDR faces:
- Adoption complexity: Cortex XDR may face challenges in adoption due to the complexity of its deployment and configuration process, particularly for organisations with limited cybersecurity expertise.
- Scalability concerns: Ensuring scalability to support the increasing volume of data generated by large enterprises and high-traffic networks can be a challenge.
By integrating extensive data sources, employing advanced analytics, and capitalising on seamless ecosystem integration, Palo Alto Networks Cortex XDR delivers a powerful defence mechanism, ready to tackle cyber threats.
Cortex XSIAM
Palo Alto takes XDR a step further with their Cortex XSIAM platform. XSIAM stands for eXtended Security Intelligence and Automation Management. It is designed to be at the centre of SOC activities, replacing SIEM and other specialty products. The key capabilities are:
- Security Information and Event Management (SIEM) delivers all common SIEM functions;
- Threat Intelligence Platform (TIP) aggregates, scores, and distributes threat intelligence data;
- Extended Detection and Response (XDR) gathers telemetry from any source for unrivalled detection coverage and accuracy;
- Endpoint Protection Platform (EPP) prevents endpoint attacks with a proven endpoint agent;
- Attack Surface Management (ASM) provides embedded attack surface management (ASM) capabilities for an attacker’s view of your organisation;
- Identity Threat Detection and Response (ITDR) uses machine learning and behavioural analysis to profile users and entities and alert on behaviours that may indicate a compromised account or malicious insider;
- Security Orchestration, Automation, and Response (SOAR) automates nearly any use case with hundreds of built-in playbooks;
- Cloud Detection and Response (CDR) analyses cloud audit, flow, and container host logs together with data from other sources;
- Management, reporting, and compliance simplifies operations, centralising all configuration, monitoring, and reporting functions.
Cisco XDR/SecureX
Cisco’s current XDR solution, SecureX, will go end of life on July 31, 2024. Their new XDR solution will simply be called: Cisco XDR.
SecureX was primarily a security platform aimed at providing visibility and control across the Cisco security portfolio. Cisco XDR focuses specifically on advanced threat detection, investigation, and response across multiple security layers, offering deeper integration with Cisco and third-party security solutions, enhanced scalability and performance, as well as potential improvements in user interface and experience for more intuitive security operations. Here are the six most important aspects of Cisco XDR:
- Comprehensive integration: Cisco XDR integrates not only with Cisco’s own security products but also with a wide range of third-party tools. This integration capability ensures that different security components can work together harmoniously, providing a cohesive defence mechanism across the entire digital landscape.
- Unified visibility: The platform offers a unified view across all data sources, including endpoints, networks, and cloud environments. This centralised visibility is crucial for effective security monitoring and management, allowing teams to quickly detect and respond to incidents from a single interface.
- Advanced analytics: Cisco XDR utilises advanced analytics to detect unusual behaviour and potential threats. By leveraging machine learning and other sophisticated techniques, it provides deeper insights into security data, helping to identify complex attack patterns that might otherwise go unnoticed.
- Automated response: Automation is a key feature of Cisco XDR, enabling rapid containment and remediation of threats. This capability allows organisations to reduce response times and operational overhead, enhancing their ability to manage and mitigate risks.
- Proactive threat hunting: The platform supports proactive threat hunting initiatives, empowering security teams to actively search for and neutralise potential threats before they escalate. This proactive approach is essential for maintaining a strong security posture in today’s dynamic threat environment.
- Scalability and flexibility: Cisco XDR is designed to be scalable and flexible, accommodating the growing and evolving needs of businesses.
Two challenges that Cisco XDR faces:
- Complexity in hybrid environments: Managing security across hybrid environments, including on-premises, cloud, and multi-cloud environments, may present challenges.
- Coordination with legacy systems: Integrating with legacy security systems and tools may be challenging for Cisco XDR, particularly in organisations with complex and outdated infrastructures.
These features make Cisco XDR a robust choice for enterprises looking to strengthen their cybersecurity defences by leveraging a platform that provides integration, visibility, and effective automation in threat detection and response.
TEHTRIS XDR Platform
The TEHTRIS XDR Platform is recognised for its comprehensive approach to cybersecurity, aiming to protect organisations against advanced and evolving cyber threats. Here are six key aspects that define the TEHTRIS XDR Platform:
- Unified cyber defence: TEHTRIS XDR integrates multiple security technologies, including EDR, NDR, Mobile Threat Defense (MTD), and SIEM, into a single platform. This unification allows for seamless security operations and a consolidated view of threats across all vectors.
- Real-time threat detection and response: The platform is engineered to detect and neutralise threats in real time. Leveraging advanced algorithms and machine learning, it can identify malicious activities and automate responses to mitigate threats promptly, thereby reducing potential damages.
- Global threat intelligence: TEHTRIS XDR benefits from a continuously updated global threat intelligence feed, which enhances its capability to recognise and react to new and emerging threats. This intelligence is critical for staying ahead of attackers and ensuring that defensive measures are both current and effective.
- Automated security orchestration: Automation is a core feature of the platform, facilitating streamlined and efficient security operations. By automating routine tasks and responses, the platform helps reduce the workload on security teams, allowing them to focus on more strategic issues.
- Scalability and adaptability: Designed to cater to businesses of all sizes, from small enterprises to large corporations, the TEHTRIS XDR platform is scalable and adaptable. It can be configured to meet the specific needs of an organisation, ensuring that security grows in tandem with the business.
- Comprehensive compliance support: The platform provides robust tools for compliance management, including detailed logging, reporting, and analysis capabilities. These features are invaluable for organisations needing to adhere to regulatory requirements and maintain high standards of security governance and documentation.
Two challenges that TEHTRIS XDR faces:
- Operational overhead: Managing the operational overhead associated with maintaining and updating TEHTRIS XDR's extensive threat intelligence databases and analytics engines may be challenging for some organisations.
- Customisation complexity: Even though scalability and adaptability is possible, the customisation of security policies and response actions to suit the specific needs and threat profiles of different organisations may be complex and time-consuming.
Overall, the TEHTRIS XDR Platform stands out for its integration of security solutions, real-time protection capabilities, and its emphasis on automation and intelligence-led threat mitigation. These aspects make it a powerful ally for organisations aiming to strengthen their cybersecurity posture against ever-changing threats.
Trellix XDR Platform
The Trellix XDR Platform is a cybersecurity solution that emerged from the integration of McAfee Enterprise and FireEye, combining their strengths to offer advanced threat detection and response capabilities. Here are the six most important aspects of the Trellix XDR Platform:
- Unified security operations: The platform integrates multiple security technologies, such as endpoint protection, network security, and cloud analytics, into a single platform. This consolidation provides a unified view and control point for security operations, enhancing the ability to detect and manage threats across various vectors.
- Advanced threat intelligence: The platform leverages the vast threat intelligence networks of its predecessor organisations, providing deep insights into emerging threats and malicious actors. This intelligence is continuously updated and fuels the platform's predictive capabilities to identify and counteract sophisticated cyberattacks.
- Automated detection and response: Trellix XDR uses automation to streamline the detection, investigation, and response processes. This automation reduces the time and manual effort required to respond to incidents, increasing operational efficiency and reducing the window of opportunity for attackers.
- Behavioural analytics: By employing behavioural analytics, it identifies unusual behaviour patterns within the network, endpoints, and applications that may indicate a security breach. This approach helps to pinpoint stealthy attacks that might otherwise evade traditional detection mechanisms.
- Cross-platform coverage: The platform is designed to protect a variety of IT environments, including cloud, on-premise, and hybrid systems. Its flexibility ensures comprehensive coverage and adaptability to different organisational needs and technology landscapes.
- Scalability and customisation: Trellix XDR is scalable to accommodate organisations of all sizes, from small businesses to large enterprises. It also offers customisation options to tailor security policies and responses to the specific needs and risks of the organisation, allowing for a more personalised security approach.
Two challenges that Trellix XDR faces:
- Integration challenges: Integrating Trellix XDR with existing McAfee and FireEye security products and platforms may present technical challenges, particularly in environments with diverse security architectures.
- Data overload: Aggregating and analysing vast amounts of security data generated by Trellix XDR may lead to challenges in effectively prioritising and responding to security alerts.
Overall, the Trellix XDR Platform combines robust intelligence, advanced analytics, and extensive automation to offer a powerful defence mechanism against complex and evolving cyber threats, making it suitable for a wide range of organisational needs.
Cybereason XDR
Cybereason XDR is a cybersecurity solution designed to provide comprehensive protection across an organisation's entire digital environment. Here are six key aspects of Cybereason XDR:
- Comprehensive data integration: It integrates data from multiple sources including endpoints, networks, and cloud services. This extensive data collection enables a more holistic view of the threat landscape, allowing for better detection and response capabilities.
- Advanced threat detection: Utilising machine learning and behavioural analytics, Cybereason XDR can identify complex, multi-stage threats. This includes detecting cyberattacks such as ransomware, phishing, and zero-day exploits, often before they can cause significant damage.
- Automated real-time response: The platform provides automated response capabilities that can mitigate threats in real-time. This rapid response reduces the window of opportunity for attackers to cause harm and helps limit the scope and scale of breaches.
- Proactive threat hunting: Cybereason XDR offers threat hunting tools that empower security teams to proactively search for and neutralise potential threats. This proactive approach is critical for pre-empting attacks and managing hidden risks that automated systems may not catch.
- Operational efficiency: By automating many aspects of the threat detection and response process, Cybereason XDR helps improve the operational efficiency of security teams. It reduces the burden of manual tasks, allowing teams to focus on strategic security initiatives.
- Customisable security policies: The platform allows organisations to customise security policies to suit their specific needs and threat profiles. This flexibility ensures that security measures are as effective as possible and tailored to the unique challenges your organisation faces.
Two challenges that Cybereason XDR faces:
- Alert fatigue: The XDR solution may face challenges in mitigating alert fatigue due to the high volume of security alerts generated by its comprehensive threat detection capabilities.
- Customisation complexity: Even though the security policies and response actions can be customised to suit specific needs, some organisations find it complex and time consuming for this solution.
Cybereason XDR is designed for organisations looking for a robust, efficient, and adaptive security solution capable of addressing the full spectrum of cyber threats across diverse digital environments.
Latest XDR report by third-party analysts
The most recent assessment of XDR by third-party analysts, such as Gartner and Forrester, dates back to 2021. Three years is a long time in cybersecurity land. Many developments have taken place since then.
A more recent report related to XDR is the Q4 2023 Magic Quadrant by Gartner on Endpoint Protection Platforms. Two of our partners mentioned above, CrowdStrike and Palo Alto Networks, are recognised as Leaders. You’ll find Cisco and Trellix as Niche Players and Cybereason as Visionary.
While consulting analyst reports can be insightful, it's equally vital to consider user feedback. Evaluating active end-user perspectives from the various solution providers offers valuable insights. It shows how they rate the evaluation and procurement phases, how they experienced the integration and deployment phase, the quality of the service and support, and overall product capabilities.
Nomios’ XDR vendors
At Nomios, we understand that selecting the ideal XDR solution and seamlessly integrating it into your existing network can be a complex process. Our team of experienced experts is dedicated to simplifying this journey for you. We work closely with your organisation to understand your specific needs, budget limitations, and long-term goals using a consultative approach.
Our goal is to provide you with the insights and guidance needed to make an informed decision. Once the right XDR solution is identified, our skilled professionals will handle the implementation process, ensuring minimal disruption to your operations. With Nomios by your side, you can harness the power of XDR technology confidently, knowing that your security is safe.
Do you want to know more about this topic?
Our experts and sales teams are at your service. Leave your contact information and we will get back to you shortly.